If you want to debug/inspect/analyze SSL/TLS traffic made by curl, you can easily do so by setting the environment variable SSLKEYLOGFILE to a file path of your choice (for storing the secrets), and then point Wireshark to use this file.
Let’s see how:
In Wireshark, go to Edit -> Preferences -> Protocols -> SSL -> (Pre)-Master-Secret log filename, and set the path:
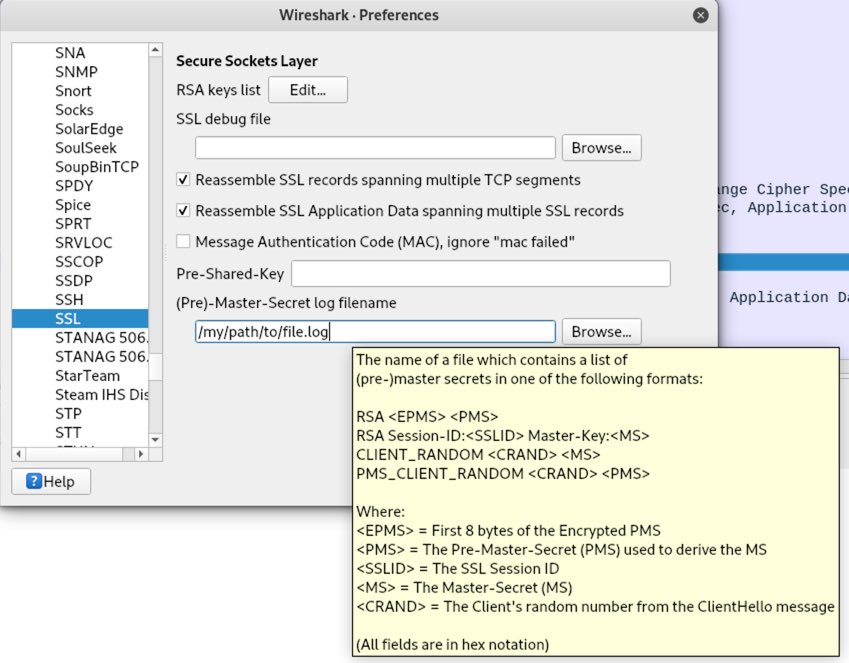
Then start the Wireshark capture.
In your shell, you can now set the environment variable and make a request:
$ SSLKEYLOGFILE=/my/path/to/file.log curl https://example.com
(export the variable if you want it to be available to all apps in your current session)
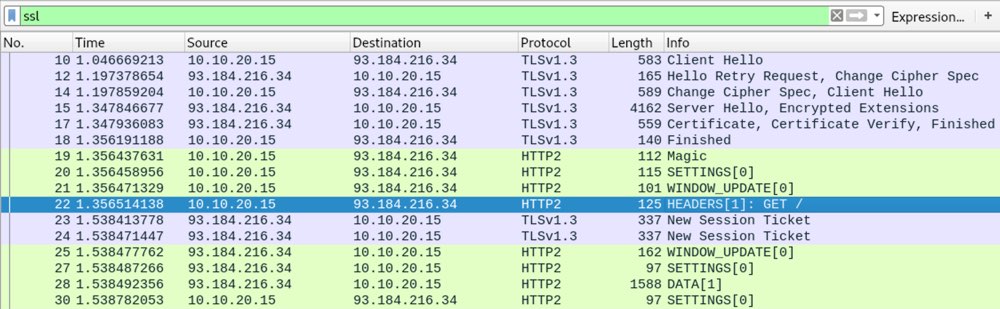
In Wireshark, you should now be able to see the decrypted traffic:
Version note: I used curl 7.65.1 with OpenSSL.
✉️ Have a comment? Please send me an email.