Reading sniffed SSL/TLS traffic from curl with Wireshark
If you want to debug/inspect/analyze SSL/TLS traffic made by curl, you can easily do so by setting the environment variable SSLKEYLOGFILE to a file path of your choice (for storing the secrets), and then point Wireshark to use this file.
Let’s see how:
In Wireshark, go to Edit -> Preferences -> Protocols -> SSL -> (Pre)-Master-Secret log filename, and set the path:
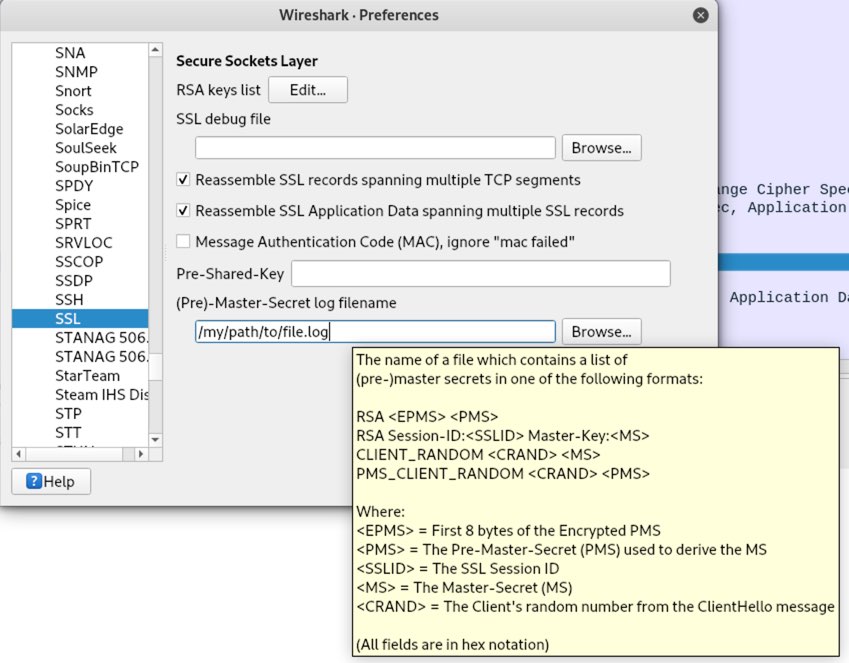
Then start the Wireshark capture.
In your shell, you can now set the environment variable and make a request:
$ SSLKEYLOGFILE=/my/path/to/file.log curl https://example.com
(export the variable if you want it to be available to all apps in your current session)
In Wireshark, you should now be able to see the decrypted traffic:
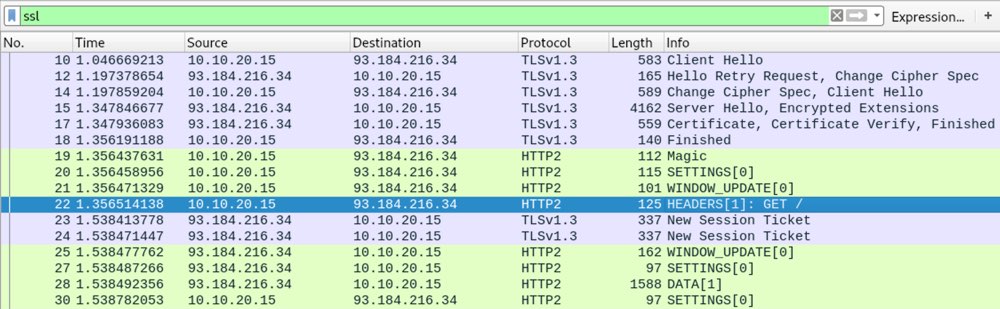
Version note: I used curl 7.65.1 with OpenSSL.


Like to comment? Feel free to send me an email or reach out on Twitter.
Did this or another article help you? If you like and can afford it, you can buy me a coffee (3 EUR) ☕️ to support me in writing more posts. In case you would like to contribute more or I helped you directly via email or coding/troubleshooting session, you can opt to give a higher amount through the following links or adjust the quantity: 50 EUR, 100 EUR, 500 EUR. All links redirect to Stripe.